Most state notification statutes have similar components, New York State does have some important differences. This document provides guidelines on compliance and notification laws in New York State in the event of a data security cyber-attack.
Continual collaborative efforts from your people, processes and technology will deliver a robust data security framework.
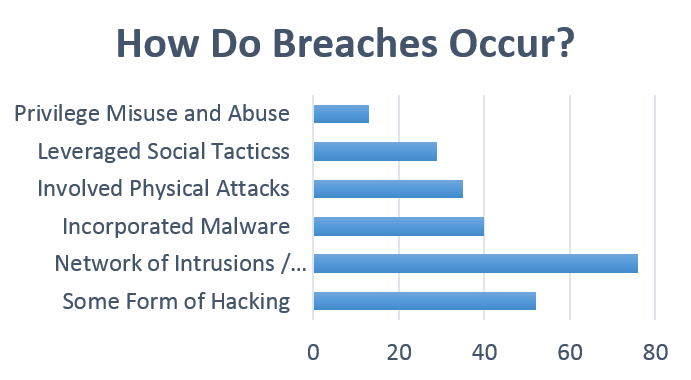
Source: Department of Homeland Security | Data Breach Investigations Report
State entities and persons or businesses conducting business in New York who own or license computerized data which includes private information must disclose any breach of the data to New York residents.
NYS Information Security Breach and Notification Act
The NYS Information Security Breach and Notification Act is comprised of section 208 of the State Technology Law and section 899-aa of the General Business Law. Copies of these sections can be found below.
Section 208 of the State Technology Law
Section 899-aa of the General Business Law
State entities are also required to notify non-residents, see Information Security Policy P03-002 V3.4 Part 12.

Source: Department of Homeland Security | Data Breach Investigations Report
NYS Information Security Breach and Notification Act
Persons or Businesses Conducting Business in New York
(Section 899-aa of the General Business Law) MUST notify three (3) NYS offices:
- NYS Attorney General;
- NYS Division of State Police;
- Department of State’s Division of Consumer Protection.
Breach Notification Law. NOTE: State entities subject to section 208 of the State Technology Law that experience breaches of computerized data which includes private information must file notices of with the New York Attorney General; Department of State’s Division of Consumer Protection; and the Office of Information Technology Services’ Enterprise Information Security Office.
Description of Breach (select all that apply):
Loss or theft of device or media
(e.g., computer, laptop, external hard drive, thumb drive, CD, tape);
Internal system breach;
Insider wrongdoing;
External system breach (e.g., hacking);
Inadvertent disclosure;
Other specify): ________________________
BASIC STEPS TO COMPLIANCE AND NOTIFICATION
Detection of a threat is solid security. Take steps to analyze and evaluate your organization’s threat landscape:
Eliminate non-essential data;
Ensure that critical security policies and procedures are being put into practice;
Collect and analyze incident data to drive ongoing security effectiveness.
The New York State Office of CyberSecurity(OCS) assists local governments and school districts through integrated training events and through its audit function to:
-
- Develop IT policies, including breach notification procedures;
- Limit and restrict access rights to systems and equipment;
- Develop and test disaster recovery plans;
- Configure strong access controls on firewalls;
- Provide information security awareness training to all personnel;
- Regularly tracking/monitoring system activity (all remote access);
- Provide for secured off-site storage of back up data;
- Maintain an up-to-date inventory of software and equipment; and
- Maintain up-to-date virus protection.

Source:
The Department of Homeland Security (DHS) www.dhs.gov/cyber.
https://www.llis.dhs.gov/content/2013-data-breach-investigations-report
http://www.dhses.ny.gov/ocs/breach-notification/
To report a cyber incident: https://forms.us-cert.gov/report/ or (888) 282-0870.